Why Build a Homelab?

My reasons to build this homelab was to monitor and secure my home network. I also wanted to learn how to selfhost applications, websites, media servers etc. Its my digital playground to study.
This way I also avoid the most common question in IT:
📞: Have you tried turning it off and on again❓
Rack

The network rack is made of a 3U 19” Wall Mount Vertical Rack Bracket that has the Mikrotik 24 Port Switch. The pfSense firewall is mounted on the 1U server rack shelf, I used motherboard standoffs to secure it. The network card is connected with a PCI-E x4 Extension Cable Riser.
- 3U 19” Wall Mount Vertical Rack Bracket
- 1U Server Rack Shelf
- PCI-Express PCI-E x4 Extension Cable Riser
The rack bracket itself is only 18cm deep, so it extremely compact. The MikroTik CRS326-24G-2S+RM is a short depth rack mount model measuring 440mm x 144mm x 44mm so it fits nicely on the wallmount.


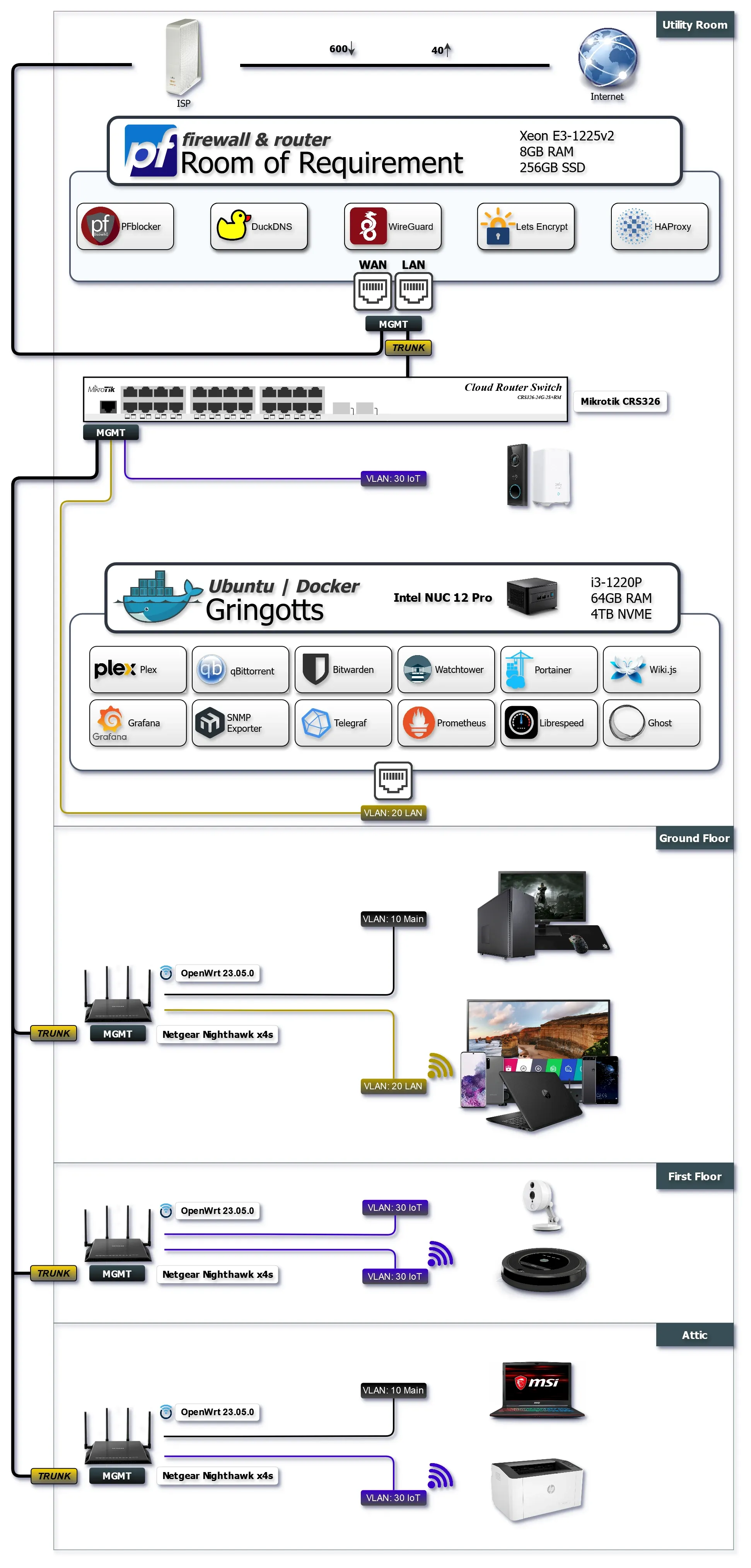
Homelab Diagram
My homelab consists of a bridged Arris cablemodem that is connected to my custom pfSense firewall. The pfSense firewall handles all the VLAN routing and is connected with a VLAN trunk to the Mikrotik CRS326. The Mikrotik sends on the VLAN's to all the OpenWrt Netgear R7800 accesspoints.
The Intel NUC is the server that runs all the docker containers. It is where we stream media from Plex and hosts this website using Ghost CMS among other things.
pfSense allows me to eleminate bufferbloat using traffic shapers, and configure reverse proxy to Cloudflare so I dont expose services directly. It acts as a WireGuard VPN server so I can access the Docker containers, but most off when I use WireGuard I route all traffic through the Firewall and pfBlocker-NG. pfBlocker blocks ads but also web tracking, malware and ransomware. Wich is especially usefull when connected to public WiFi.
💡 Tip: pfBlockerNG can block ads and prevent access to malicious sites on mobile devices like Android and iOS phones
Vlan Overview
The VLAN's are pretty straightforward.
- VLAN10 MAIN is for managing the network, and applications.
- VLAN20 LAN is the main network and it’s a combination between wired and wireless devices, my work stations, laptops, mobile devices, smart tv etc.
- VLAN30 IoT camera's, printer, and doorbell are only allow internet access.
- VLAN99 MGMT is where all network devices are located.
| VLAN ID | Subnet | Info | Access |
|---|---|---|---|
| 10 | 172.16.10.0/24 | Main | ALL |
| 20 | 172.16.20.0/24 | LAN | 20, 30 |
| 30 | 172.16.30.0/24 | IoT | NONE |
| 99 | 172.16.99.0/24 | MGMT | ALL |
Firewall
pfSense is what I use for the firewall. It brings a lot of excellent reasons to the table:
- Open-source: Because it is open-source, not only is pfSense free to use, but community members can contribute to the code to make it a better software.
- User-friendly: pfSense’s interface is fairly simple, and quite easy to use.
- Well-supported: pfSense regularly has security and feature updates. It also has a documentation site and a well-informed and knowledgeable support forum.
I used a build guide from pfSense JDM’s Mini-ITX pfSense builds to assemble my ideal firewall that fits my utility closet.
| Device | Name |
|---|---|
| CPU | Xeon E3-1225 |
| Motherboard | GA-B75TN |
| RAM | 8GB DDR3L |
| Storage | 256 Sata SSD Phison SSEP256 |
| NIC | Intel 4 Port I340-T4 |
pfSense is used for:
- Network segmentation with VLANs
- Firewall rules
- Access apps through Wireguard VPN
- Apply traffic shaping (QoS)
- DHCP Server
- DNS Server
- Certificates Manager (for HAProxy/VPN)
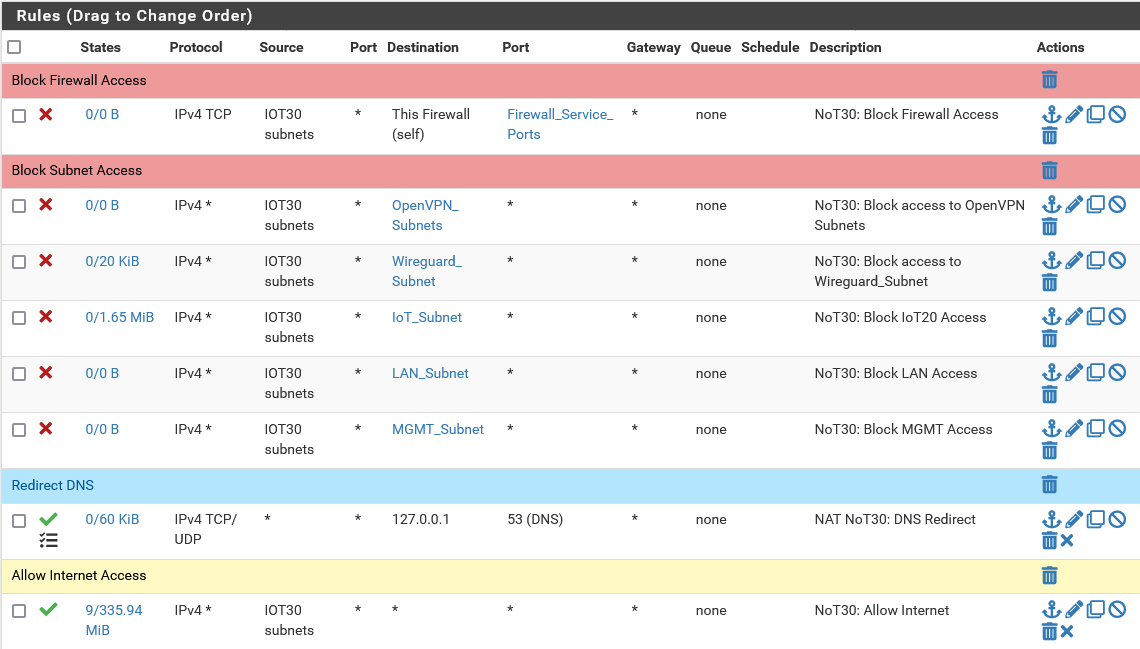
Example firewall rules for VLAN30 IoT:
Tom Lawrence has number of good setup guides for pfSense that I use:
- Basic Setup and Configuring pfsense Firewall Rules For Home
- How To Setup VLANS With pfsense & UniFI. Also how to build for firewall rules for VLANS in pfsense
- Office Network Design and Planning with VLANs, LLDP, Rules, IoT, Guest using UniFi & pfsense
Switch

The Mikrotik CRS326-24G-2S+RM is a 24 Gigabit port switch with 2 x SFP+ cages in 1U rackmount case. It is configured as a layer 2 switch, pfSense handles all hte routing. It fits all my requirements:
- Low power
- No PoE
- Low cost
- SFP+ for the NUC 12 Pro
The three Netgear r7800 Nighthawk's X4S AC2600 dont require PoE. Its a very good deal compared to the UniFi USW-Pro-24 wich sells for €700.
I configured a Bridge Vlan using The Network Trips guide in RouterOS. This tutorial is excellent.
Incase you plan on using it with SWOS I recommend checking out:
Router on a Stick VLAN Configuration with SwOS on the Mikrotik CRS328-24P-4S+RM Switch by Michael Schnerring.
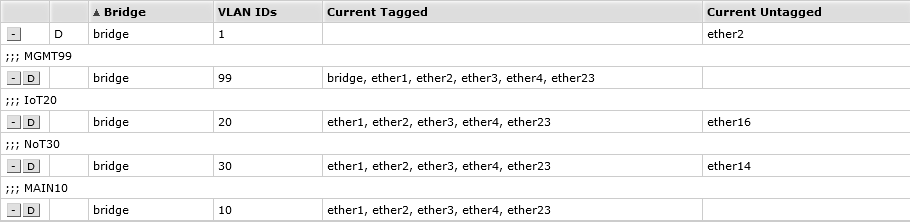
Accesspoints

The Nighthawk X4S AC2600's are configured to run as "Dumb" Access Points. The term dumb is used since the AP will not provide administrative duties such as routing, firewall, DHCP, or DNS, as these will be performed by the main router or other device.
I installed OpenWrt 23.05.0 on all three of them. The R7800 still uses the Switch Config VLAN configuration. I choose to install OpenWrt because its superior to the stock firmware, and is actively updated so any vulnerabilities are closed shortly after they are discovered.
Wireless Networks
| VLAN ID | Info | SSID | Mode | Width |
|---|---|---|---|---|
| 20 | LAN | The Floo Network | 5ghz | 40Mhz |
| 30 | IoT | The Leaky Cauldron | 2.4ghz | 20 Mhz |
❗ Warning: Firmware update mean age is 230 days, meaning that the average device received an update in the last eight months. In that time frame 114 CVEs have been attributed to the Linux kernel. Home Router Security Report 2022
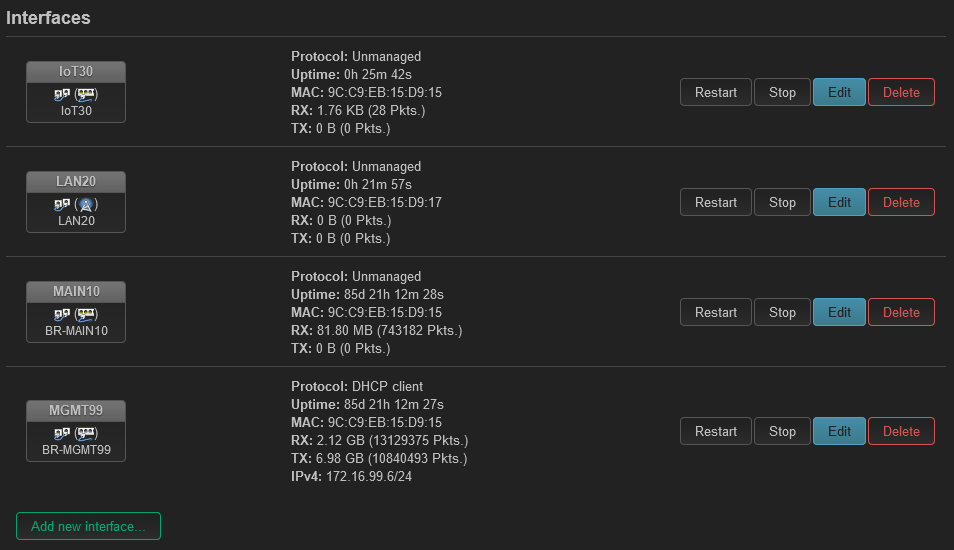
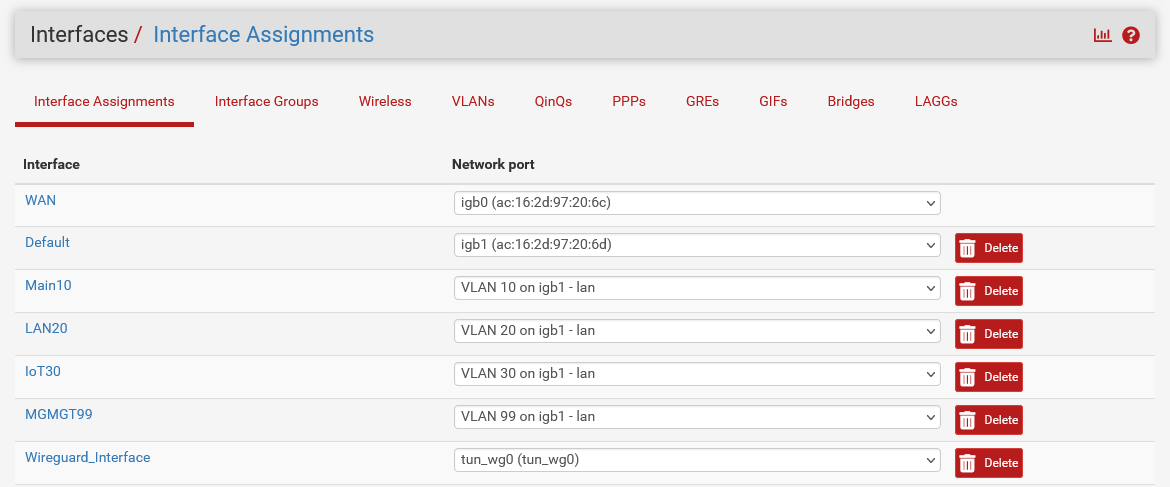
interface section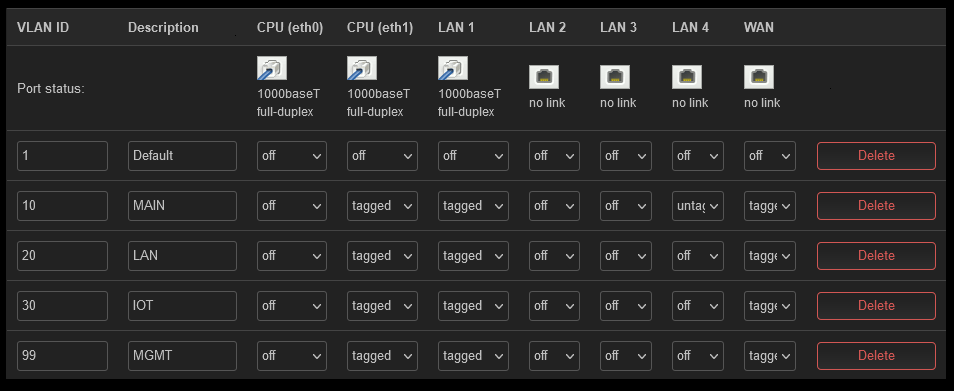
DNS
pfSense acts as the DNS Resolver and pfBlockerNG is a package for pfSense and helps to enhance the security by allowing me to block malicious IP addresses, domains, and countries. My DNS request are checked agains blocklists, if a match is found the request is denied.
Tom Lawrence has an excellent setup guide for pfBlockerNG:
pfsense: Blocking Threats With pfblockerNG Lists
💡 Tip Alternatives: AdGuard Home or PiHole are also great for network-wide ads & trackers blocking
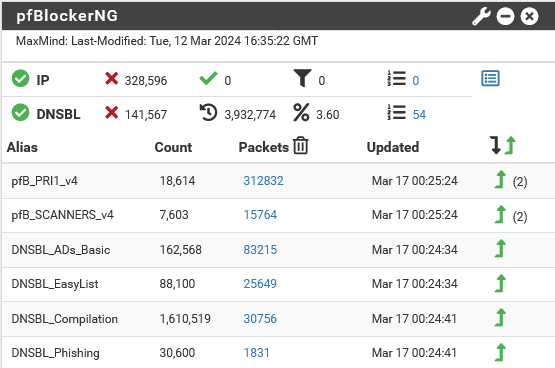
| Category | Alias | Description |
|---|---|---|
| IPv4 | PRI1 | Most reputable blocklist |
| IPv4 | SCANNERS | Searching for exposed services |
| DNSBL | ADs_Basic | ADvertisement Feeds |
| DNSBL | EasyList | Primary filter list |
| DNSBL | Compilation | hageziPro, hageziTif, PhishingArmy |
| DNSBL | Phishing | Phishing Domain Feeds |
Homelab
Server

My homelab server is a tiny Intel Nuc 12 Pro that hosts my docker containers on Linux Ubuntu Server 22.04.4 LTS. Ubuntu Server runs "headless", that means it doest have a graphical user interface. It also lacks peripherals like monitor, keyboard and mouse. That makes it more efficient.
I manage the Ubuntu Server strictly through SSH and the Docker Containers are managed with Portainer.
Its perfect because:
- Its compact
- Silent
- Upgradeable RAM and storage
- 2.5GbE NIC
- Low idle power consumption
I mainly use it for:
- Selfhosting
- Streaming media using Plex
- Downloading Linux ISO's using qBittorrent
- Hosting this website using Ghost CMS
- Network monitoring
- Grafana dashboard metrics
- Speedtesting using Librespeed
Intel Nuc 12 Pro
| Device | Name |
|---|---|
| CPU | i3-1220P 10 Cores |
| RAM | 64GB DDR4 SO-DIMM |
| Storage | 2TB Crucial MX500 |
| Storage | 2TB Lexar M710 NVME |
| OS | Ubuntu Server 22.04.4 LTS |
💡 Tip: A cheap alternative is to look at second hand small form factor pc's. Serve the Home as a excellent project: Introducing Project TinyMiniMicro Home Lab Revolution
Containers
The containers are managed with Portainer. I use it as an overview of all running services, the UI is easy to use and most of all the container logs are very useful.
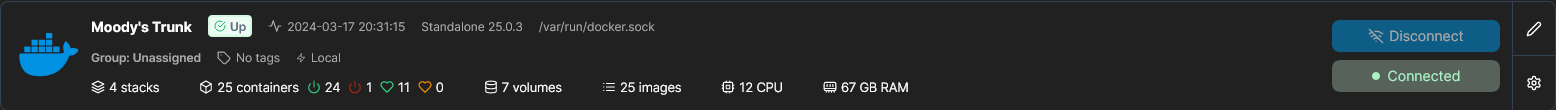
| Name | Description |
|---|---|
| Wiki.js | Knowledgebase |
| Prometheus | Monitoring toolkit |
| Grafana | Visualization platform |
| Telegraf | Collecting agent |
| Mikrotik SNMP | Monitoring switch |
| Librespeed | Lightweight speedtest |
| Bitwarden | Password manager |
| Qbittorrent | Torrent client |
| Plex | Media server |
| Watchtower | Docker container update |
| Portainer | Container management |
Network Monitoring
The main reason for the homelab was so I can monitor the network. I started out with SmokePing and started looking for an alternative monitoring stack. I ended up using Telegraf, Prometheus and Grafana.
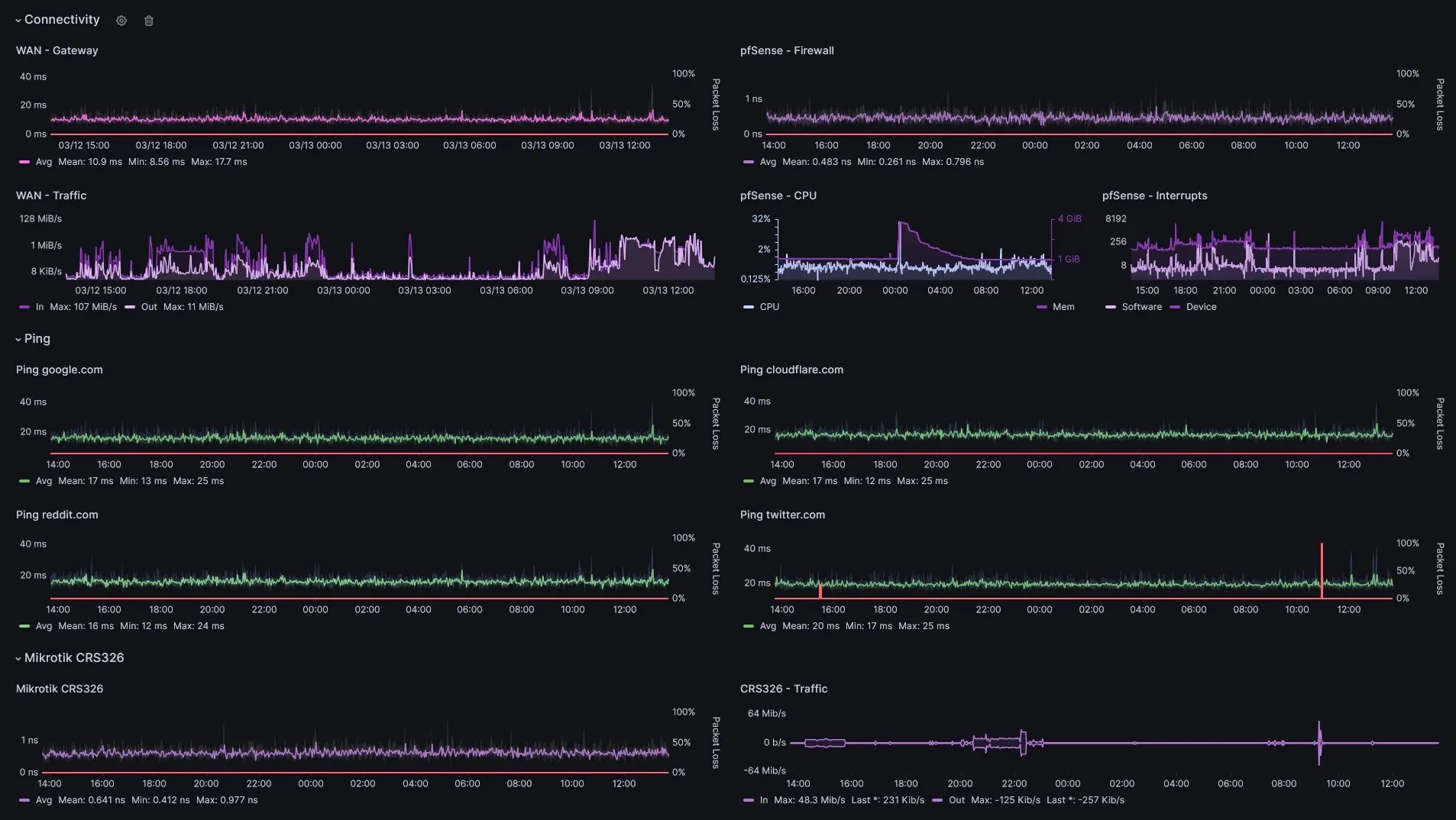
Prometheus pulls metrics from Telegraf and Prometheus Node_Exporters. These can be used to create a Dashboard in Grafana. I monitor ping response times to network devices and cloudflare, google, reddit and twitter.com. I also monitor traffic on the Mikrotik switch and Intel Nuc 12 Pro server.
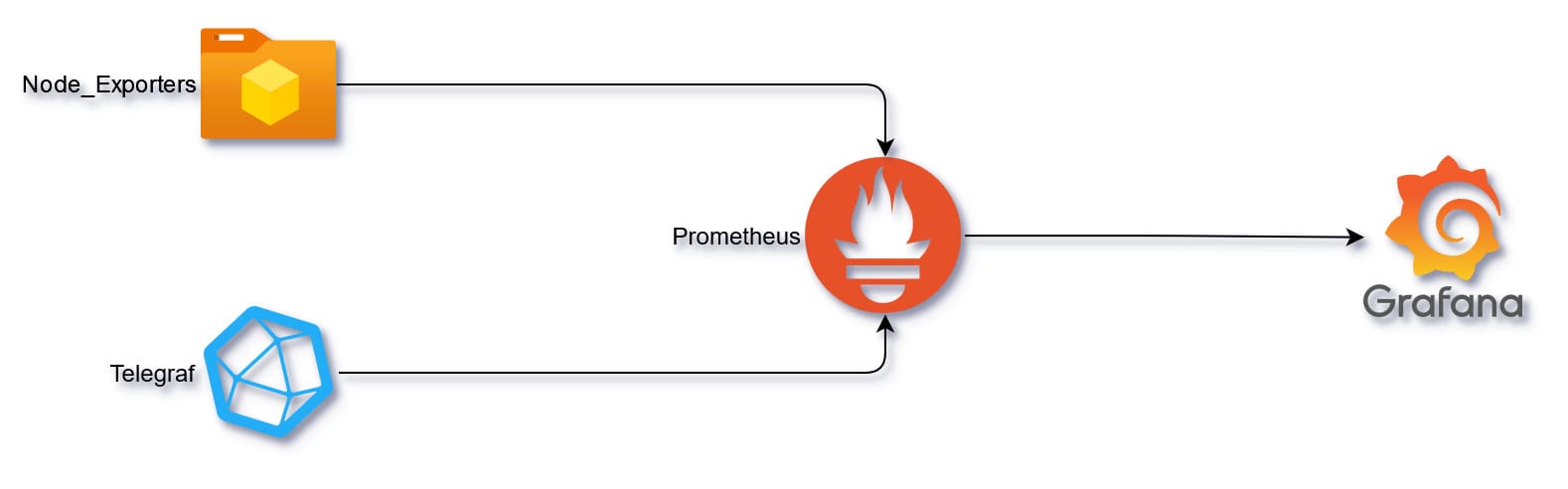
💡 With this stack I am able to monitor my home network, so I never blame "lagg" for poor gaming performance.
Conclusion
I really like where my homelab is at the moment. My only complaint is the different network vendors that makes it very complicated to manage the VLANs. If I were to start over again with a higher budget I would consider replacing the Mikrotik switch and OpenWrt R7800 with UniFi gear.
That would allow me to host a UniFi Network Application on portainer, and safe me hours of scouring forums for obscure setups(looking at you mikrotik!).