Mobile Security with WireGuard and pfBlockerNG
How I use pfSense and pfBlockerNG with WireGuard VPN, to connect safely and browse privately on Public Wi-Fi. And why you should!

Why do we need to block ads and trackers on public Wi-Fi?
A large-scale study revealed that 3.92% of the 19 milion access points are under Wi-Fi attacks, the majority (55%) of the detected attacks are ad injections. When users connected to these public Wi-Fi networks they can be at risk to various kinds of frauds and abuses (Gao et al., 2021, p. 1). For instance ad injectors can negatively impact a user's browsing experience, security and privacy. Thomas et al. (2015, p. 153) shows that ad injectors often monitor all of a user's browser activities such as page interactions and search queries. These behaviors are then reported to third parties for tracking and advertisement selection. Blocking these third-party trackers offers the best strategy against online tracking. The use of a network wide ad blocker combined with a VPN tunnel could be an effective solution for mobile devices on public Wi-Fi.
- Why do we need to block ads and trackers on Public Wi-Fi?
- How to Block Ads and Trackers on Public Wi-Fi
- Tools
- VPN AdBlocker
- Conclusion
- References:
How do we block ads and trackers?
Virtual Private Networks (VPNs) provide a method of communications over untrusted public networks (Odonkor, et. al., 224). They enables us to tunnel all traffic back to a trusted location, such as a Small Office/Home Office (SOHO) network, where it can be further routed to the internet. This adds an essential layer of privacy (Jodoin, 2013, p. 2). All DNS queries to download ads will be prevented at the DNS level using a network-wide adblocker.
This can be achieved without the use of a browser extension enabling ease of use across a broad variety of mobile platforms including Windows, Linux, iOS and Android.
Another benefit is the use of the SOHO network resources such as access to files hosted on network shares and Network-Attached Storage (NAS) or access to an IP Based camera or surveillance system.
Tools:

Network-wide Adblocker: pfBlockerNG
pfBlockerNG-devel is a firewall package for pfSense that can actively monitor every DNS request performed on the network (Zientara, 2016, p. 325). This makes it very effective regardless of the browser used, and is even capable of blocking in-app advertisements.
pfBlockerNG: Filter Lists
pfBlockerNG can be configured using filter lists, we will use some of the most common and curated lists available. The first one named EasyList and its goal is to remove ads from English Web pages, this will be supplemented with EasyList Dutch to remove ads from Dutch Web pages. The third list is EasyPrivacy which aims to protect the end users' privacy by blocking Web trackers (Pujol-Gil, Hohlfeld, & Feldmann, 2015, p. 94). These list showed a significant reduction (96-98%) of domains that track and aggregate users activity across sites (Wills & Uzunoglu, 2016, p. 11).

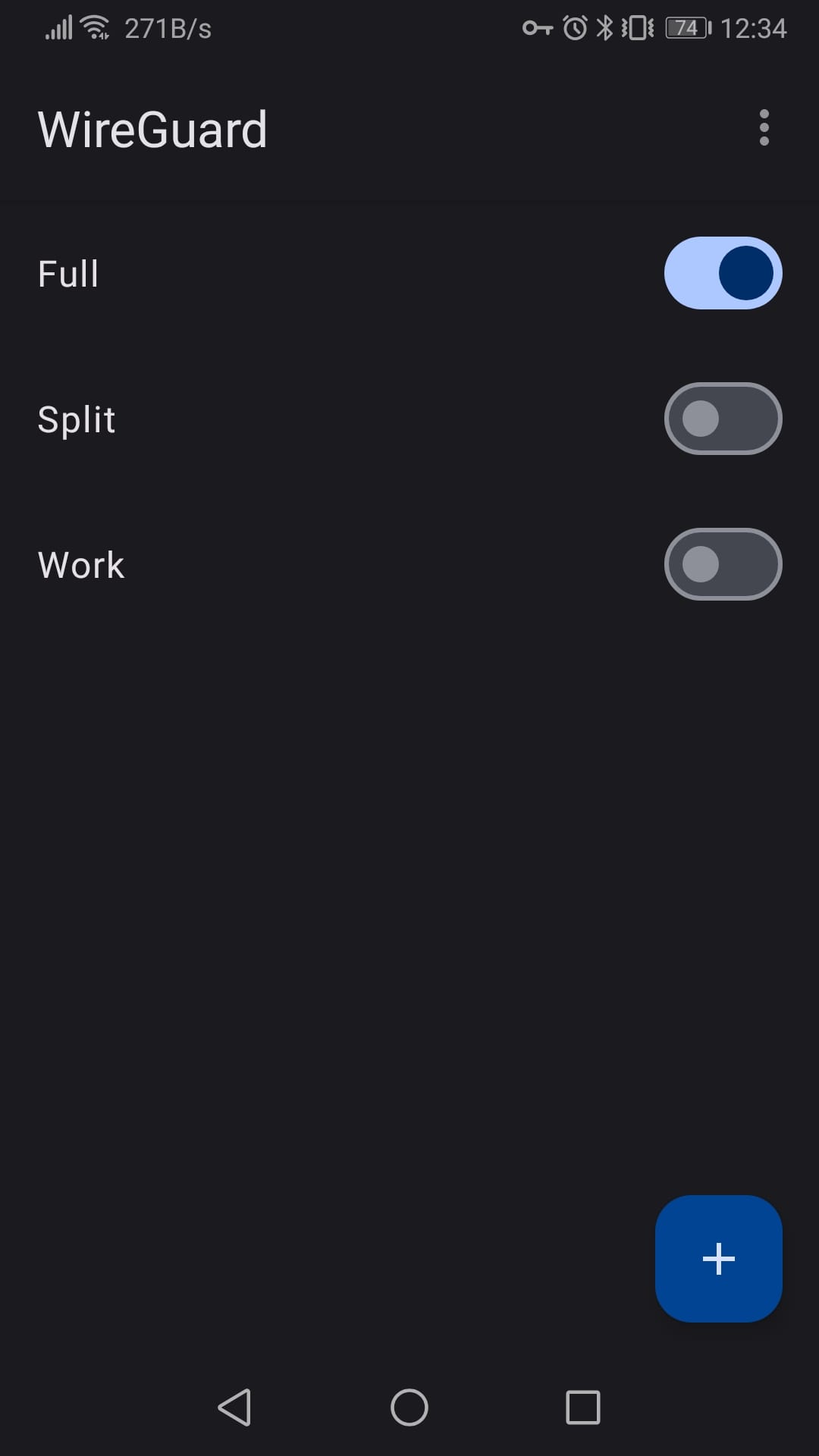
WireGuard VPN Tunnel
WireGuard is a modern VPN that is more secure, more performant, and easier to use compared to solutions like OpenVPN (Donenfeld, 2017, p. 1). WireGuard will be installed as a package in pfSense and all the internet traffic will be rerouted through pfSense to make use of the filtering capabilities of pfBlockerNG-devel.
To route all traffic through the tunnel to a specific peer, we added the default route 0.0.0.0/0 for IPv4 to AllowedIPs in the [Peer] section of our clients WireGuard config files:
AllowedIPs = 0.0.0.0/0
VPN AdBlocker
pfBlockerNG and WireGuard combined act as an private network-based DNS filter for all devices connected to the network and blocks ads and trackers at the network level, preventing them from reaching your devices. This is achieved by establishing a secure network tunnel using WireGuard to our SOHO network, thereby intercepting DNS requests and filtering out known ad-serving domains and tracking servers.
As a result, ads and trackers are blocked before they even reach your devices, providing a seamless ad-free browsing experience across your entire network.
To assess if our pfBlockerNG WireGuard solution blocks ads, we first need to establish a baseline without any ad filtering on the mobile device. This can done by using AdBlock test from d3dward
This tool allows you to check if your adblock solution is blocking enough hosts. With a simple UI and easy UX you can check how much you have blocked. The tool tries to connect to the most common domains for different categories (ads, analytics, bug tracking, social trackers, mix and OEMs)."
Some of the most common third-party domain included in this test are:
1. google-analytics.com
2. doubleclick.net
3. googlesyndication.com
4. googleadservices.com
5. amazonaws.com
6. facebook.com
7. twitter.com
8. yahoo.com
Merzdovnik et al. (2017, p. 7) found that the great majority of third-party services belong to a relatively small number of large Internet players. Google, without question, provides the most popular third-party web services.
Overall, Google services are included by 97% of websites in their sample. The reach of Google can be credited to three service categories: analytics, advertisements, and content delivery network (CDN) services.
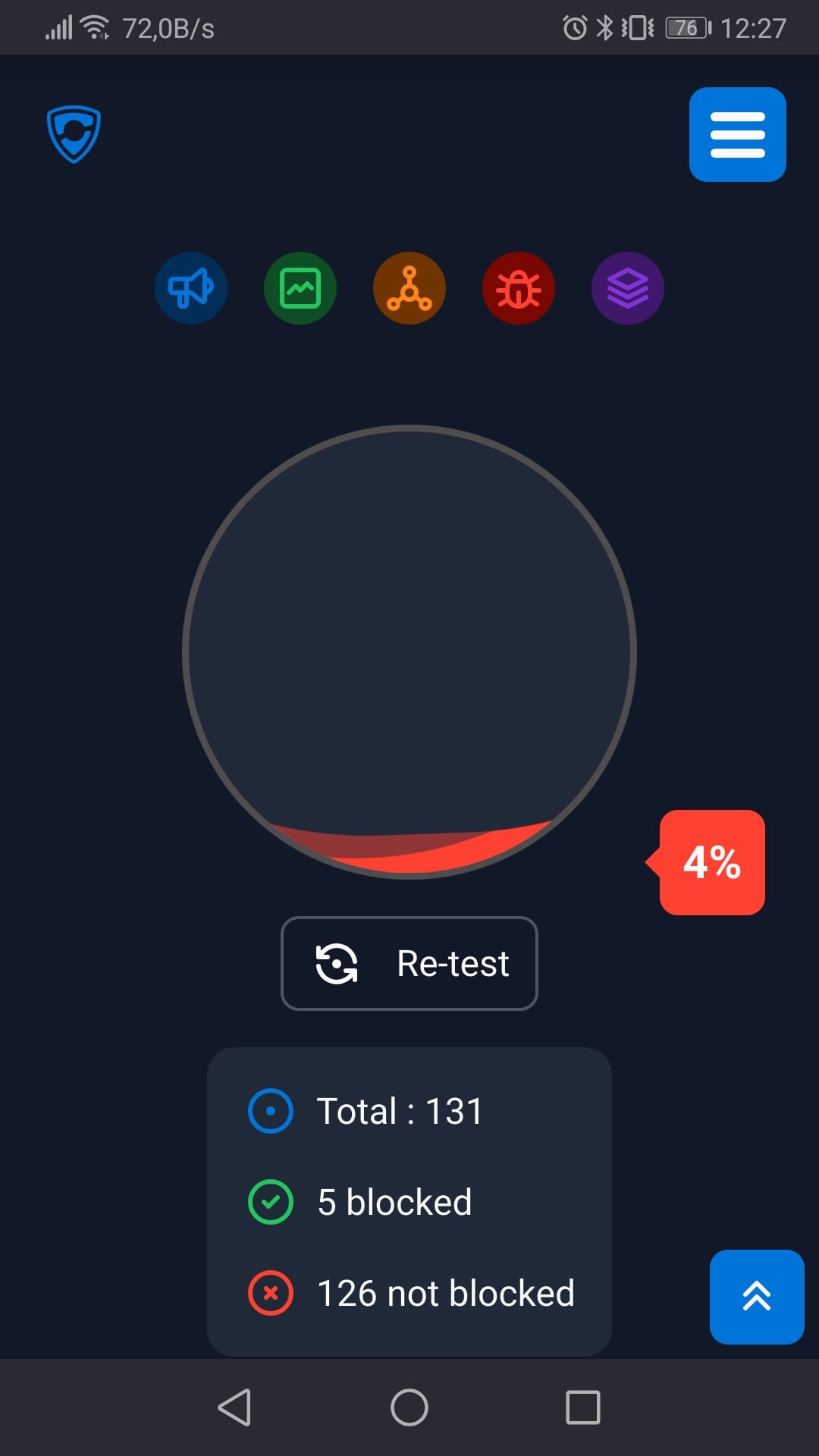
Ad-Blocking Off: What Happens When You Are Unprotected?
With our mobile device connected to public Wi-Fi results in only 4% block rate.
With VPN and pfBlockerNG
To assess if our solution increases our chance of blocking these third-party domains we first have to connect our mobile device to our local network using WireGuard.
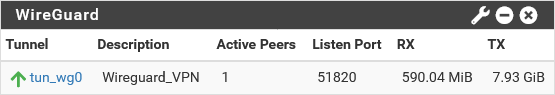
To check if the connection is established we can view the WireGuard widget on our pfSense Dashboard:
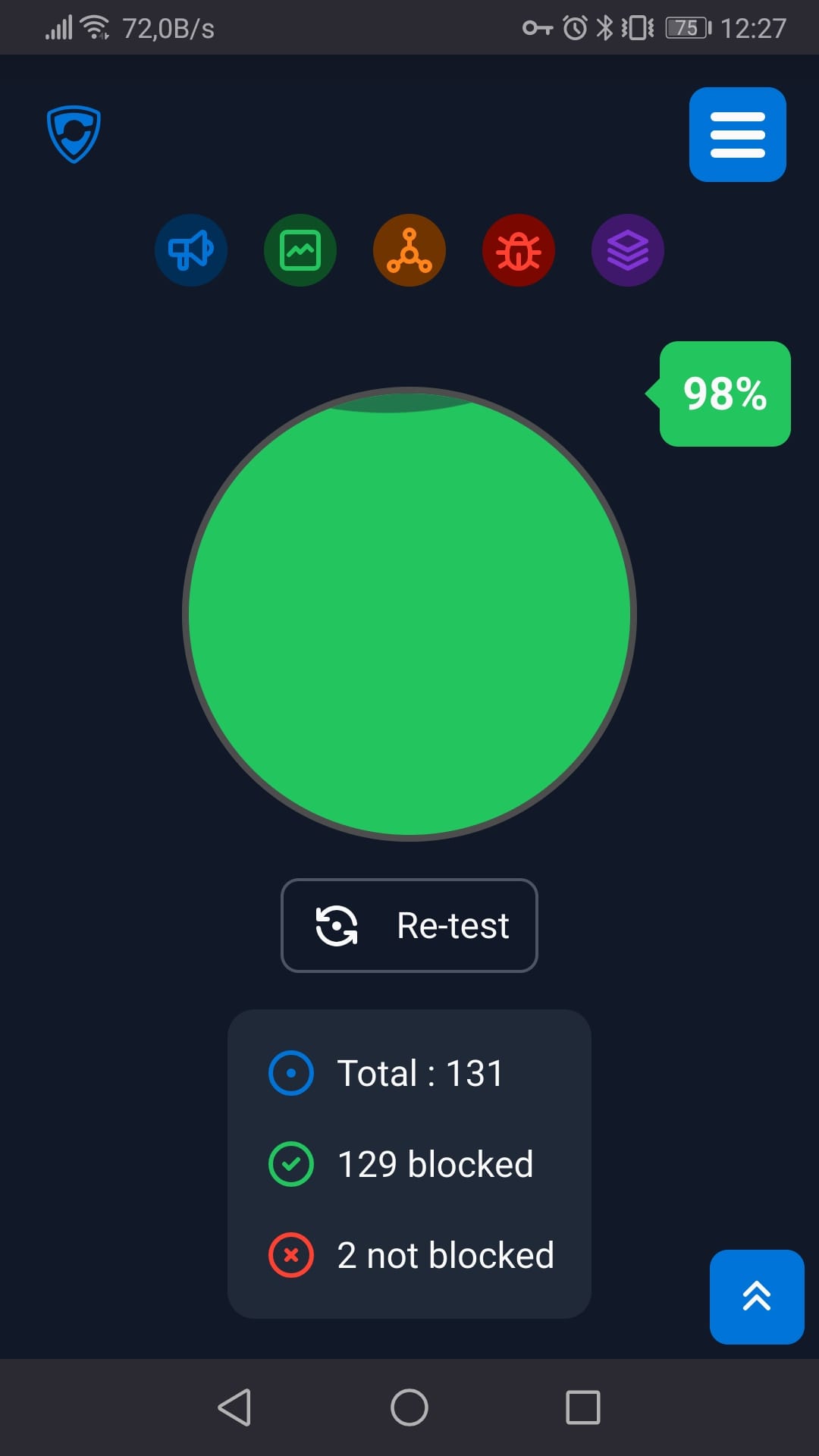
Once the connection is active we can Re-test the d3ward AdBlock test. Now we see our blocking rate is at 98%.
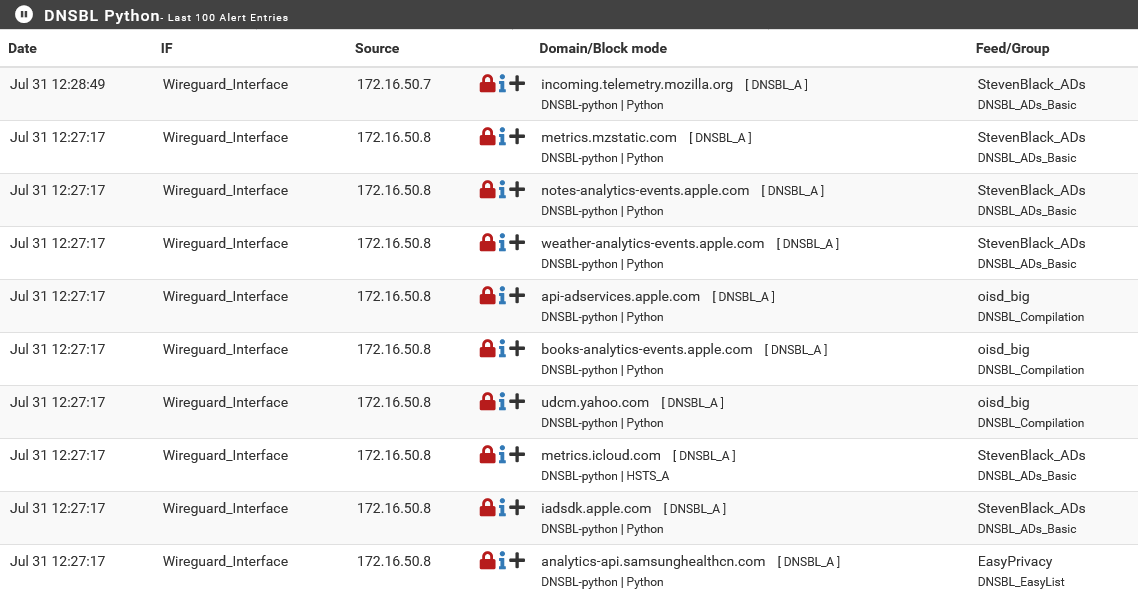
We can verify that all the DNS request are filtered by our pfBlockerNG instance by viewing our pfBlockerNG Alerts and filter Alerts for the Wireguard_Interface. Here we see a snippet of some of the requested domains:
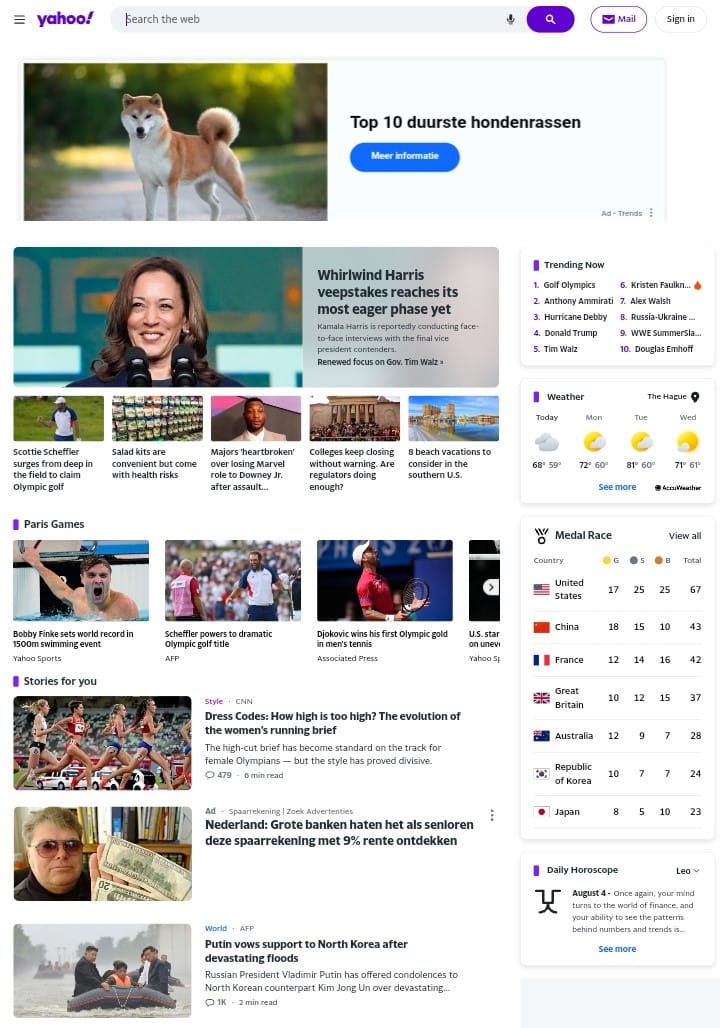
In browser adblock test
Yahoo.com was chosen for this in brows test because it displays many advertisements that distract a user who is strongly focused on reading solely the content. Fig 7 shows that main page that contains several ads.
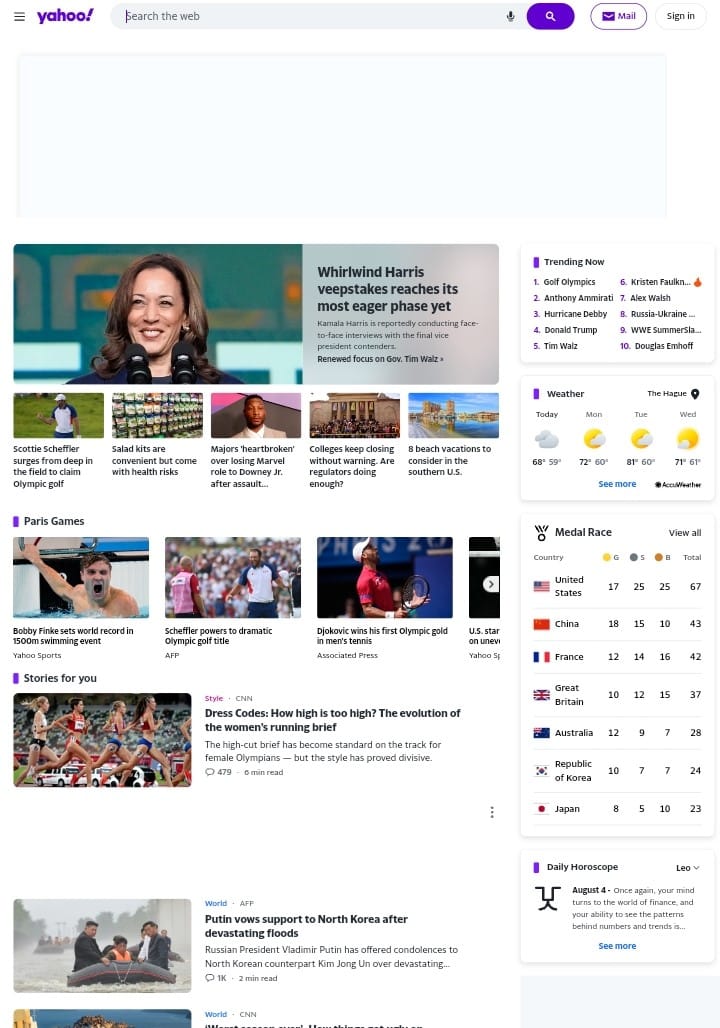
After implementing WireGuard and pfBlockerNG, the result in Figure 8 shows the same page on the Yahoo.com is no longer displaying large ads that distract the user.
Conclusion
Enabling our VPN Adblocking increases our blocked items by an impressive 2478.8%, from 5 blocked items to 129 blocked items. This setup is very simple to use, requiring only the activation of the Wireguard VPN tunnel to our SOHO location. pfBlockerNG filters all DNS requests before they exit the pfSense firewall to the internet. All required software is open source, making it very cost-effective and highly scalable. Plus, no additional plugins or software installations are needed on client devices.
References:
-
Donenfeld, J. A. (2017). WireGuard: Next generation kernel network tunnel. Network and Distributed System Security Symposium.
-
Gao, D., Lin, H., Li, Z., Qian, F., Chen, Q. A., Qian, Z., Liu, W., Gong, L., & Liu, Y. (2021). A nationwide census on wifi security threats: Prevalence, riskiness, and the economics. In Proceedings of the 27th Annual International Conference on Mobile Computing and Networking (MobiCom '21) (pp. 242–255). Association for Computing Machinery. https://doi.org/10.1145/3447993.3448620
-
Jodoin, E. (2013, November 24). SOHO remote access VPN. Easy as pie, Raspberry Pi... GIAC (GSEC) Gold Certification (D. Shinberg, Advisor). SANS Institute. https://sansorg.egnyte.com/dl/sljGCVLmJA
-
K. Thomas, et al. (2015). Ad injection at scale: Assessing deceptive advertisement modifications. In 2015 IEEE Symposium on Security and Privacy (pp. 151-167). IEEE. https://doi.org/10.1109/SP.2015.17
-
Merzdovnik, G., Huber, M., Buhov, D., Nikiforakis, N., Neuner, S., Schmiedecker, M., & Weippl, E. R. (2017). Block me if you can: A large-scale study of tracker-blocking tools. In 2017 IEEE European Symposium on Security and Privacy (EuroS&P) (pp. 319-333). IEEE.
-
Patel, K., & Sharma, P. (2017). A review paper on pfsense – an open source firewall introducing with different capabilities & customization. International Journal of Advance Research and Innovative Ideas in Education, 3, 635-641.
-
Pujol-Gil, E., Hohlfeld, O., & Feldmann, A. (2015). Annoyed users: Ads and ad-block usage in the wild. In Proceedings of the 2015 Internet Measurement Conference.
-
Wills, C. E., & Uzunoglu, D. C. (2016). What ad blockers are (and are not) doing. In 2016 Fourth IEEE Workshop on Hot Topics in Web Systems and Technologies (HotWeb) (pp. 72-77). IEEE.
-
Zhang, Z., Zhang, Y. Q., Chu, X., & Li, B. (2004). An overview of virtual private network (VPN): IP VPN and optical VPN. Photonic Network Communications, 7, 213-225.
-
Zientara, D. (2016). Mastering pfSense: Master the art of managing, securing, and monitoring your network using the powerful pfSense 2.3. Packt Publishing.